


Part of our working week is auditing current websites of potential clients. This involves reporting on how it views on different systems, as well as the...
In the crowded world of e-commerce, it is only natural that you want to get the leg up against your competitors. As such, it is crucial...



You know what web design is. You’re quite familiar with it, in fact. You’ve been doing web design for years and have been very successful in...



The world of business is becoming increasingly digitalized. In fact, your current customers and even potential clients can access your entire product range and services from...



/k_fdob7_uq8 is the misspelt word for DOB in HTML . The DOB input field is an essential element in web forms that require age verification, such...



A well-designed website is an asset to any company, helping it excel in digital marketing, rank well in search engines, and be competitive in the market....

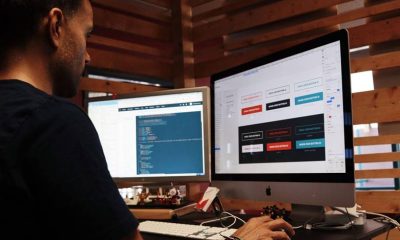

The internet is rife with pre-made website templates. In contrast, there is a lack of sites that provide the kind of experience that would be ideal...
In an era when remote healthcare is becoming more accessible, it is critical for the healthcare industry to address privacy and security concerns to ensure patient...



In today’s fast-evolving digital landscape, cybersecurity is more important than ever. With the increasing frequency and sophistication of cyberattacks, organizations must take proactive measures by partnering...



Elite security comes in handy when safeguarding high-risk environments. Think about threats to terrorism and organized crime. At the core, high-profile individuals, valuable property, and sensitive...